Q 1) As a Security Engineer you need to ensure that
specified user can manage assignments for other administrators and implement
Azure AD Privileged Identity Management ( PIM ).
Which role should you assign the users to achieve the goal ?
Select TWO correct answers.
A. Global Admin
B. Privileged Role Admin
C.
Security Reader
D.
Security Admin
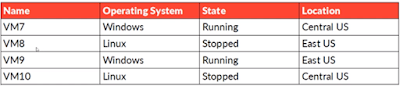
Q 2) You have created Azure Log Analytics workspace in RG7
in Central US region. Which virtual machines can be enrolled in Log Analytics
workspace as shown in the table below:
A.
VM7 only
B.
VM7 & VM10 only
C. VM7, VM8, VM9 and VM10
D.
VM8 & VM9 only
Q 3) A company has set up log analytics workspace to gather
performante counters associated with thousands of on-premise servers.
Which signal type should you use to create alert rules ?
A. Metric Signal Type
B.
Activity log Signal Type
C.
Application Insights
D.
Log alerts
Q 4) A company needs to dynamically generate a resource ID
that will designate the key vaultcontaining the appropriate secret during
deployment of each identically configured Azure Virtual Machine.
How can you generate the resource ID ?
A.
Parameter file
B. Linked template
C.
Playbooks
D.
Security Baseline
Q 5) As a Security engineer you want to ensure that each
subscription has identical role assignments which make use of Privilege
Identity Management ( PIM ).
Which of these can meet your goal ?
A.
Automation account
B.
Multifactor Authentication (MFA)
C. Azure Blueprints
D.
Azure Stream Analytics
Q 6) Which users can enable Azure AD Privileged Identity
Management ( PIM ) for the below Azure Subscription ?
A. User7 and User9 only
B.
User7 only
C.
User8 Only
D.
User8 and User7 only
Q7) As a Security Engineer you are tasked to enable HTTPS
for Azure Web app which is hosted on an on-premise server which you want to
migrate to Azure.
What should be your approach to meet the goal ?
A. Export private key from on-prem
and save the key as PFX file, encrypted using triple DES
B.
Export private key from on-prem and save the key
as PFX file, encrypted using triple AES256
C.
Export public key and save the key as APP file
D.
Export public key and save the key as CER file
Q 8) Identify which virtual machines can create MDM Security
Baselines for the below Azure Subscription.
A. VM1
B.
VM2 and VM3
C.
VM1, VM2 and VM3
D.
VM4
Q 9) You have synced on-premises identities to Azure AD. You
don't want users with CustomerName attribute beginning with "AMIT"
shouldn't be allowed to sync to Azure AD.
What should you do ?
A.
You should configure Firewall on the subnet
B.
Use conditional access policies
C. Use Synchronization Rules Editor
to create an attribute-based filtering rule
D.
Use Multi-factor authentication (MFA) to block
attributes
Q 10) With regard to alerts for SQL Database and Azure
Synapse Analytics, which of the following alert will be invoked when an
application generates a faulty SQL statement in the database with medium
severity ?
A. A possible vulnerability to SQL
Injection
B.
Potential SQL Brute Force attempt
C.
Potential SQL injection
D.
Unusual export location
Q 11) Where should you store logs which should meet the
following requirements :
-- Support Kusto Query Language to query logs
-- Retain logs for one year
-- Administrative effort should be minimized
A.
Azure Blob Storage
B.
Azure Data Factory
C. Log Analytics workspace
D.
Azure Functions
Q 12) Which user roles can push trusted images in an Azure
Container Registry where you have enabled content trust. The solution should
use principle of least privilege.
Select TWO correct answers.
A.
Owner
B. AcrlmageSigner
C. AcrPush
D.
AcrPull
Q 13) As a Security Engineer you want to download and
retrieve log data for analysis.
Which Azure command line tool should you use ?
A.
Robocopy
B.
Kibana
C. AzCopy
D.
DocumentDB
Q 14) Which resources can be protected by Azure Defender for
the below subscription ?
A. Con7, Storage7, RM7 only
B.
Con7, Vnet7, Storage7 and RM7
C.
Con7 and Vnet7 only
D.
Vnet7 and RM7 only
Q 15) Which authentication method should you use if you want
log into Windows using your Azure Active Directory credentials from a federated
domain, or a managed domain that is configured for seamless single sign-on (
SSO ) for pass-through and password hash authentication ?
A. Active Directory - Integrated
B.
Active Directory - Password
C.
Windows Authentication
D.
Service principal object
Q 16) Which TWO images will be scanned for vulnerabilities
if you have enabled Azure Container Registry (ACR7) vulnerability scanning of
the images from Azure Security Center ?
Following actions is performed :
Push Linux Image named Image7 to ACR7
Push Windows Image named Image8 to ACR7
Push Windows Image named Image9 to ACR7
Modify Image7 and push new image as Image10 to ACR7
A. Image7
B. Image10
C.
Image8
D.
Image9
Q 17) Which role should you assign to a user who needs to
download images from Azure Container Registry?
Your solution should use the principle of least privilege.
A.
AcrDelete
B.
Owner
C. AcrPull
D.
AcrPush
Q 18) Which custom RBAC role definition should you configure
such that it can provide permission to read the Azure Storage Account ?
A. Actions[]
B.
NotActions[]
C.
DataActions[]
D.
NotDataActions[]
Q 19) Which object or resource gets created in Azure Active
Directory when a user registers an Enterprise Application ?
Select TWO correct answers.
A. Application Object
B. Service Principal Object
C.
Container Object
D.
Blob Storage
Q 20) What should you incorporate when implementing Update
Management in Azure Automation ?
The solution should meet the following requirements :
-- Minimizing the need to edit your deployment to update
machines
-- Automatic updates for VMs
A.
SQL query
B. Dynamic group query
C.
Azure Functions
D.
KQL query
Q 21) As a Security Engineer, you need to configure Azure
policy which should use a managed identity associated with the policy
assignment.
Which the following will meet your requirement ?
A. deploylfNotExists
B.
deploylfExists
C.
deploylfNotPresent
D.
deploylfAbsent
Q 22) You have deleted objects from your Azure AD tenant as
shown in the table below. On December 5, 2021 you have attempted to restore the
deleted objects.
Which TWO objects can be restored ?
A.
User7
B. User8
C. Group8
D.
Group7
Q 23) As a Security Engineer, you need to configure user
risk policy and sign-in policy by implementing Azure Active Directory Identity
Protection. The Azure subscription is currently linked to an Azure AD Premium
P1 tenant.
What should be your first step ?
A.
Enable Conditional Access Policy
B. Get at least an Azure AD Premium
P2 or trial license enabled
C.
Enable risk-based Multi-Factor Authentication
D.
Configure Microsoft Sentinel
Q 24) For which virtual machines Update Management can be
enabled ?
Azure Virtual Machines in a workspace is shown below:
A. VM7 and VM9 only
B.
VM8 and VM10 only
C.
VM8 and VM9 only
D.
VM7 and VM10 only
Q 25) How can you log data to an Azure Storage account for
network traffic that flows through a Network Security Group ( NSG) for 7
virtual machines ?
A.
Azure Functions
B. NSG flow log
C.
Microsoft Sentinel
D.
Azure Stream Analytics
Q 26) How can you retrieve diagnostics logs saved in a blob
container for an Azure Storage account ?
A. Storage Explorer
B.
NSG flow log
C.
Microsoft Sentinel
D.
Azure Stream Analytics
Q 27) You want to publish multiple apps in an Azure Active
Directory tenant which requires to grant tenant-wide admin consent.
Which user role can achieve this goal ?
Select TWO correct answers.
A.
Application Developer
B. Privileged Role Administrator
C. Application Administrator
D.
Billing Administrator
Q 28) You are tasked to switch off unwanted Windows features
automatically when instances of the virtual machines are provisioned using
Azure Resourcę Manager.
How can you meet your goal ?
A.
Configure Microsoft Teams
B.
Configure Storage account
C. Configure Azure Automation State
D.
Configure Key Vault
Q 29) You have turned on Automatic Provisioning from Azure
Security Center for the following virtual machines in an Azure subscription as
shown in the below table.
Microsoft Monitoring Agent can be installed on which virtual
machines ?
A. VM1, VM2, VM3 and VM4
B.
VM1, VM2 and VM3 only
C.
VM4 only
D.
VM2 and VM3 only
Q 30) An Azure subscription has subnet and virtual machines
as shown in the below tables. Which virtual machines are protected by Just In
Time ( JIT) if you have enabled JIT for all virtual machines ?
A. VM7, VM9, VM10 only
B.
VM10 only
C.
VM7, VM8, VM9 only
D. VM7, VM8, VM9 and VM10
If you have any problem so download the file to click on "Download".
I hope it's helpful for you. If you have any queries, don't hesitate to contact me.










0 comments:
Post a Comment
If you have any doubts, please let me know. I will help you.